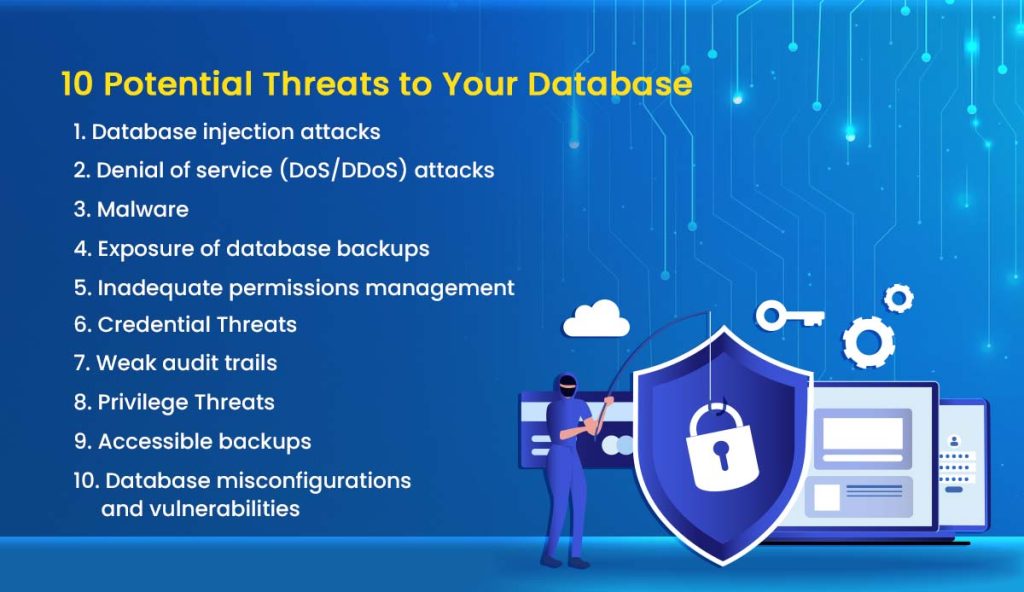
Top Database Security Threats And How To Mitigate Them . Imagine a sneaky way to. many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. that’s why we’re here to shed light on the top 5 database security threats and show you how to combat them. in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. in this comprehensive guide, we will delve into the seven most critical database security risks and threats you should be aware of and offer. guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for.
from www.esds.co.in
guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for. that’s why we’re here to shed light on the top 5 database security threats and show you how to combat them. many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. in this comprehensive guide, we will delve into the seven most critical database security risks and threats you should be aware of and offer. Imagine a sneaky way to. in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and.
Defending Against Top 10 Database Security Threats
Top Database Security Threats And How To Mitigate Them guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for. in this comprehensive guide, we will delve into the seven most critical database security risks and threats you should be aware of and offer. in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. that’s why we’re here to shed light on the top 5 database security threats and show you how to combat them. guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for. many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. Imagine a sneaky way to.
From www.cimcor.com
How to Identify Database Security Threats in 5 Steps Top Database Security Threats And How To Mitigate Them that’s why we’re here to shed light on the top 5 database security threats and show you how to combat them. many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the. Top Database Security Threats And How To Mitigate Them.
From patrickdomingues.com
Top Threats to Cloud Security and How to Mitigate Them Top Database Security Threats And How To Mitigate Them many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. in this comprehensive guide, we will delve into the seven most critical database security risks and threats you should. Top Database Security Threats And How To Mitigate Them.
From keepnetlabs.com
The Top 10 Cybersecurity Threats and How to Mitigate Them Top Database Security Threats And How To Mitigate Them in this comprehensive guide, we will delve into the seven most critical database security risks and threats you should be aware of and offer. that’s why we’re here to shed light on the top 5 database security threats and show you how to combat them. Imagine a sneaky way to. guarding against unauthorized disclosure, data breaches, and. Top Database Security Threats And How To Mitigate Them.
From backendless.com
8 Critical Database Security Best Practices To Keep Your Data Safe Top Database Security Threats And How To Mitigate Them many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for. that’s why we’re here. Top Database Security Threats And How To Mitigate Them.
From webapi.bu.edu
😍 Threats in dbms. Top Database Security Threats and How to Mitigate Top Database Security Threats And How To Mitigate Them Imagine a sneaky way to. in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for. many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches.. Top Database Security Threats And How To Mitigate Them.
From itsecuritywire.com
Top Cyber Security Threats in the TechDecade of 2020 ITSecurityWire Top Database Security Threats And How To Mitigate Them guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for. in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. in this comprehensive guide,. Top Database Security Threats And How To Mitigate Them.
From www.pdffiller.com
Fillable Online Top Database Security Threats and How to Mitigate Them Top Database Security Threats And How To Mitigate Them in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for. that’s why we’re here to shed light on the top 5 database security threats and show you how to. Top Database Security Threats And How To Mitigate Them.
From www.esds.co.in
Defending Against Top 10 Database Security Threats Top Database Security Threats And How To Mitigate Them that’s why we’re here to shed light on the top 5 database security threats and show you how to combat them. in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. in this comprehensive guide, we will delve into the seven most critical. Top Database Security Threats And How To Mitigate Them.
From webapi.bu.edu
😍 Threats in dbms. Top Database Security Threats and How to Mitigate Top Database Security Threats And How To Mitigate Them in this comprehensive guide, we will delve into the seven most critical database security risks and threats you should be aware of and offer. Imagine a sneaky way to. that’s why we’re here to shed light on the top 5 database security threats and show you how to combat them. guarding against unauthorized disclosure, data breaches, and. Top Database Security Threats And How To Mitigate Them.
From www.techuseful.com
IT Threats 5 Biggest Threats To IT, And The Best Solution To Help You Top Database Security Threats And How To Mitigate Them in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. Imagine a sneaky way to. many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. in this comprehensive guide, we will delve into the seven most critical database security. Top Database Security Threats And How To Mitigate Them.
From www.imssolutionsgroup.com
The Top 5 Database Security Threats and How to Mitigate Them Top Database Security Threats And How To Mitigate Them many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. Imagine a sneaky way to. guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for. that’s why we’re here to shed light on the top 5 database security threats and show you how to combat them. in this. Top Database Security Threats And How To Mitigate Them.
From www.radware.com
Analyzing the OWASP Top 10 Top Application Security Threats & How to Top Database Security Threats And How To Mitigate Them guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for. that’s why we’re here to shed light on the top 5 database security threats and show you how to combat them. in this comprehensive guide, we will delve into the seven most critical database security risks and threats you should be aware of. Top Database Security Threats And How To Mitigate Them.
From www.slideteam.net
Database Security Threats Ppt Powerpoint Presentation Ideas Topics Cpb Top Database Security Threats And How To Mitigate Them many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. Imagine a sneaky way to. in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. in this comprehensive guide, we will delve into the seven most critical database security. Top Database Security Threats And How To Mitigate Them.
From sectigostore.com
The Top 7 Information Security Threats & How to Mitigate Them InfoSec Top Database Security Threats And How To Mitigate Them many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. Imagine a sneaky way to. guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for.. Top Database Security Threats And How To Mitigate Them.
From www.esds.co.in
Defending Against Top 10 Database Security Threats Top Database Security Threats And How To Mitigate Them Imagine a sneaky way to. in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. that’s why we’re here to shed light on the top 5 database security threats. Top Database Security Threats And How To Mitigate Them.
From jelvix.com
What Is Database Security Standards, Threats, Protection Top Database Security Threats And How To Mitigate Them Imagine a sneaky way to. in this comprehensive guide, we will delve into the seven most critical database security risks and threats you should be aware of and offer. many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for.. Top Database Security Threats And How To Mitigate Them.
From www.lepide.com
Top Cloud Security Threats and How to Mitigate Them Top Database Security Threats And How To Mitigate Them in this blog post, we’ll explore the top 10 database security threats and discuss how you can mitigate them to ensure the safety and. that’s why we’re here to shed light on the top 5 database security threats and show you how to combat them. Imagine a sneaky way to. guarding against unauthorized disclosure, data breaches, and. Top Database Security Threats And How To Mitigate Them.
From studylib.net
Top Ten Database Security Threats Top Database Security Threats And How To Mitigate Them in this comprehensive guide, we will delve into the seven most critical database security risks and threats you should be aware of and offer. many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. Imagine a sneaky way to. guarding against unauthorized disclosure, data breaches, and misuse of information is especially important for.. Top Database Security Threats And How To Mitigate Them.